Enhancing Security in Medical Equipment with CANopen
Medical equipment increasingly relies on interconnected systems that must operate reliably and securely. In this context, the CANopen protocol plays a vital role in ensuring deterministic communication between devices. However, the growing connectivity also introduces security challenges, particularly in protecting configuration data and preventing unauthorised manipulation. This article outlines security mechanisms for CANopen devices in medical applications, derived from MicroControl’s secure configuration specification.
The Importance of Security in Medical Equipment
Medical devices are safety-critical by nature. Manipulated or misconfigured equipment may lead to incorrect diagnoses, delayed treatments, or even harm to patients. Security breaches can range from accidental misconfiguration to intentional cyberattacks. Therefore, safeguarding configuration processes is essential to maintaining the reliability of medical systems.
Secure Configuration of CANopen Devices
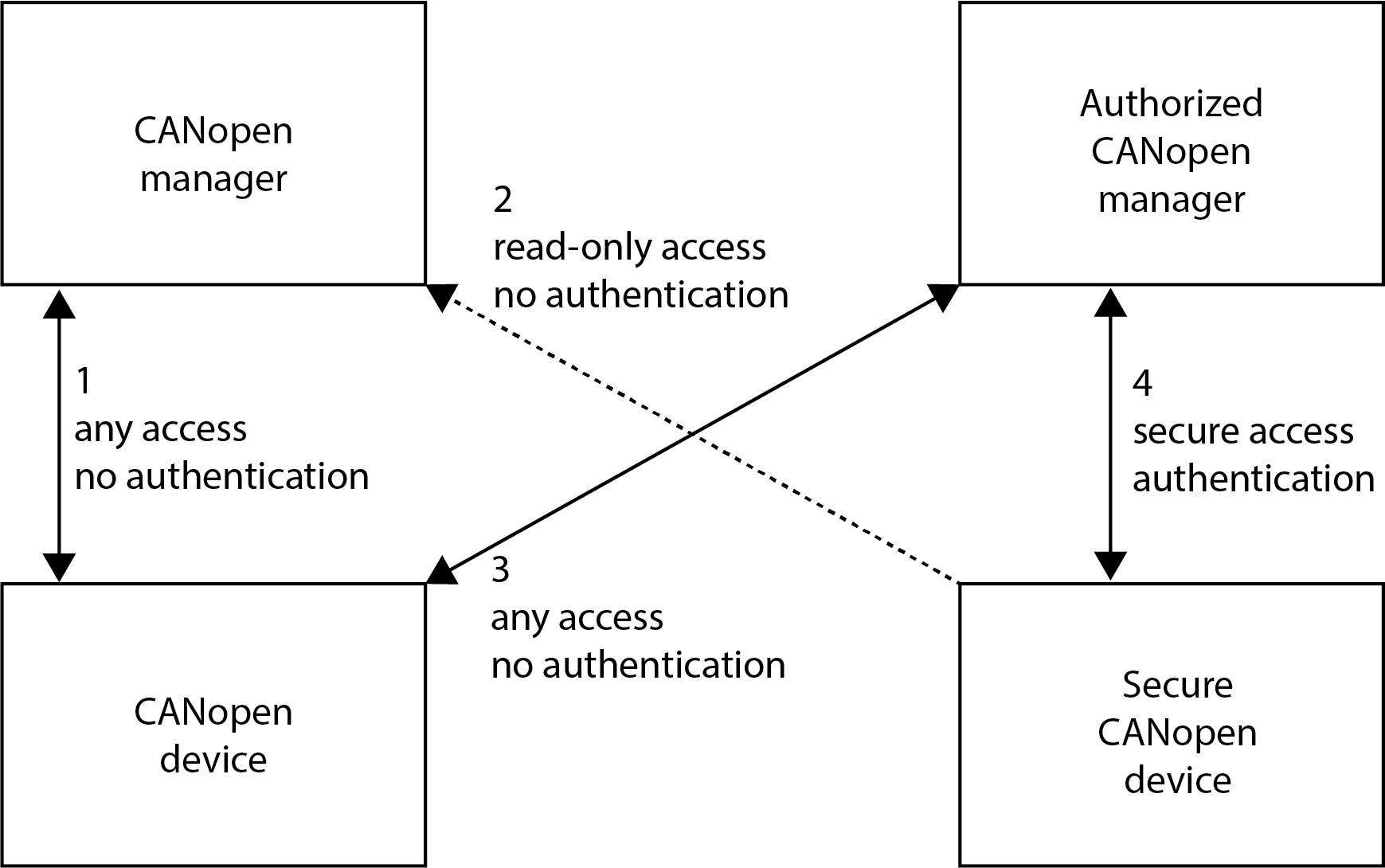
The access type (read-only, read-write, write-only) to individual data elements of a CANopen device is specified by the device EDS file. Any CANopen manager can access the data elements according to the access type (see Figure 1, connection 1 and 3).
Figure 1: Standardized vs. secure CANopen device configuration
The secure configuration concept extends the standard CANopen approach by ensuring that only authorised managers can alter configuration data. Unauthorised managers are restricted to read-only access, preventing malicious changes to critical parameters. Key requirements include:
- Securing the object dictionary without affecting CANopen conformance tests
- Authentication between authorised managers and secure devices
- Atomic write operations via secure Device Configuration Files (DCF)
- Verification of changes using checksums
Secure Configuration Process
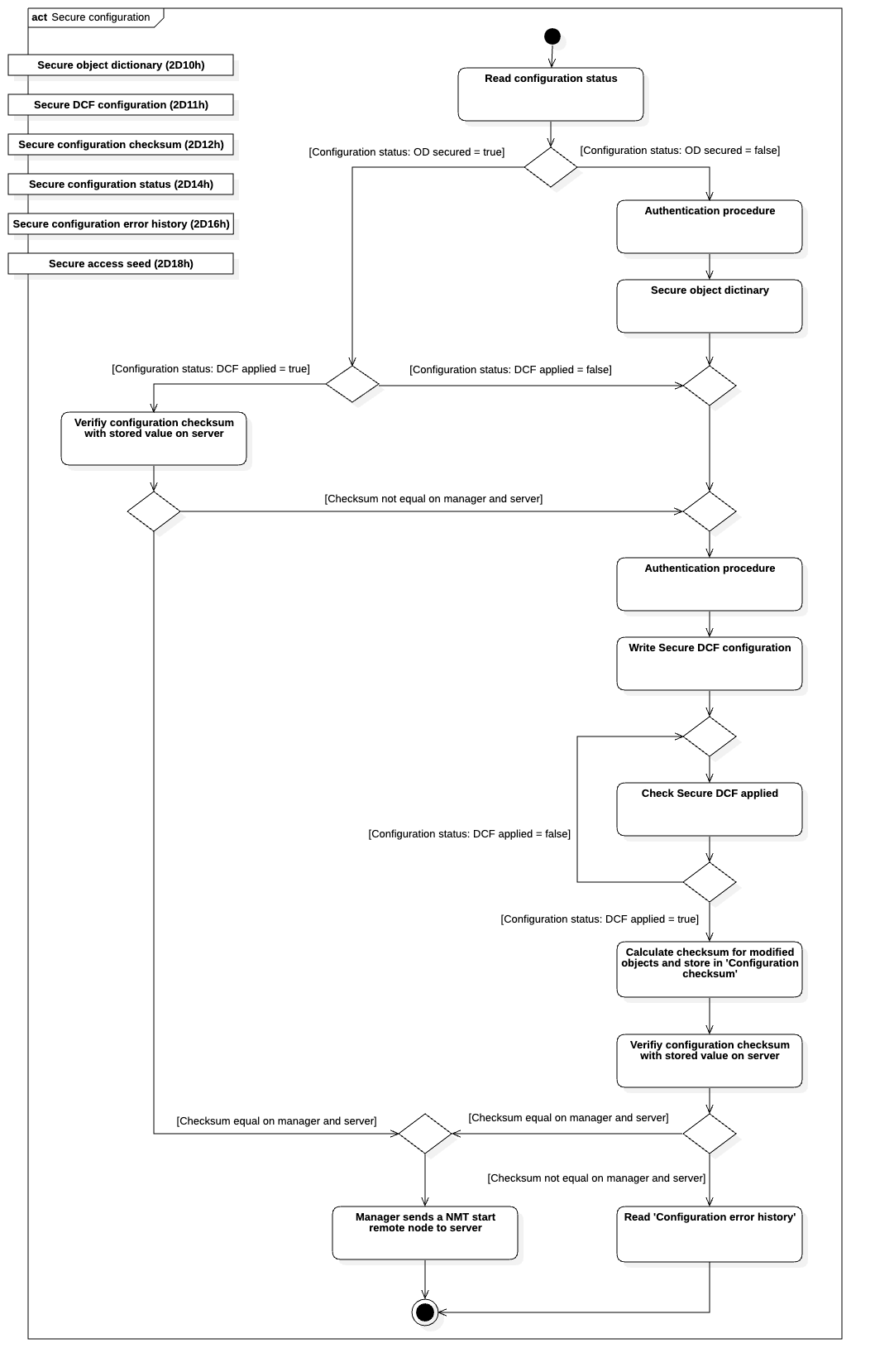
The secure configuration process (see Figure 2) ensures that only validated and authorised configurations are applied. A device in its factory state allows full configuration to pass the CANopen Conformance Test. Once secured, access to the object dictionary becomes restricted, and only Secure DCF files can be used to update its content.
Figure 2: Secure configuration process
These files are verified via checksums, guaranteeing that only authentic configurations are accepted.
Secure DCF File Format
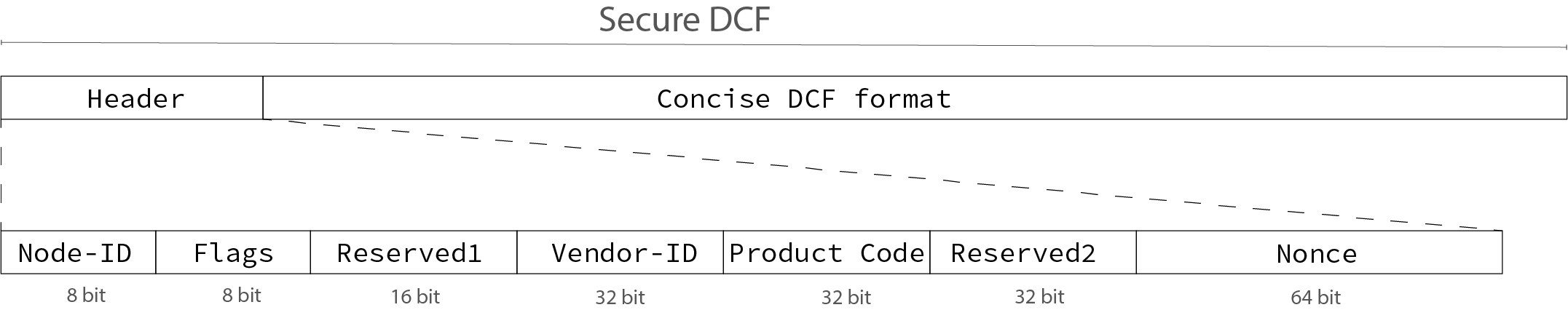
A Secure DCF file builds on the concise DCF format defined in CiA 302, with the addition of a header containing identification data such as Node-ID, Vendor-ID, Product Code, and a nonce generated during authentication (see Figure 3).
Figure 3: Secure DCF file format
This format enables both full and partial configurations:
- Full configurations are mandatory for initial setup, ensuring a trusted baseline.
- Partial configurations allow selective updates but are only valid after a successful full configuration.
Checksum verification ensures integrity, and failed operations are logged in the device’s error history.
Authentication and Object Dictionary Security
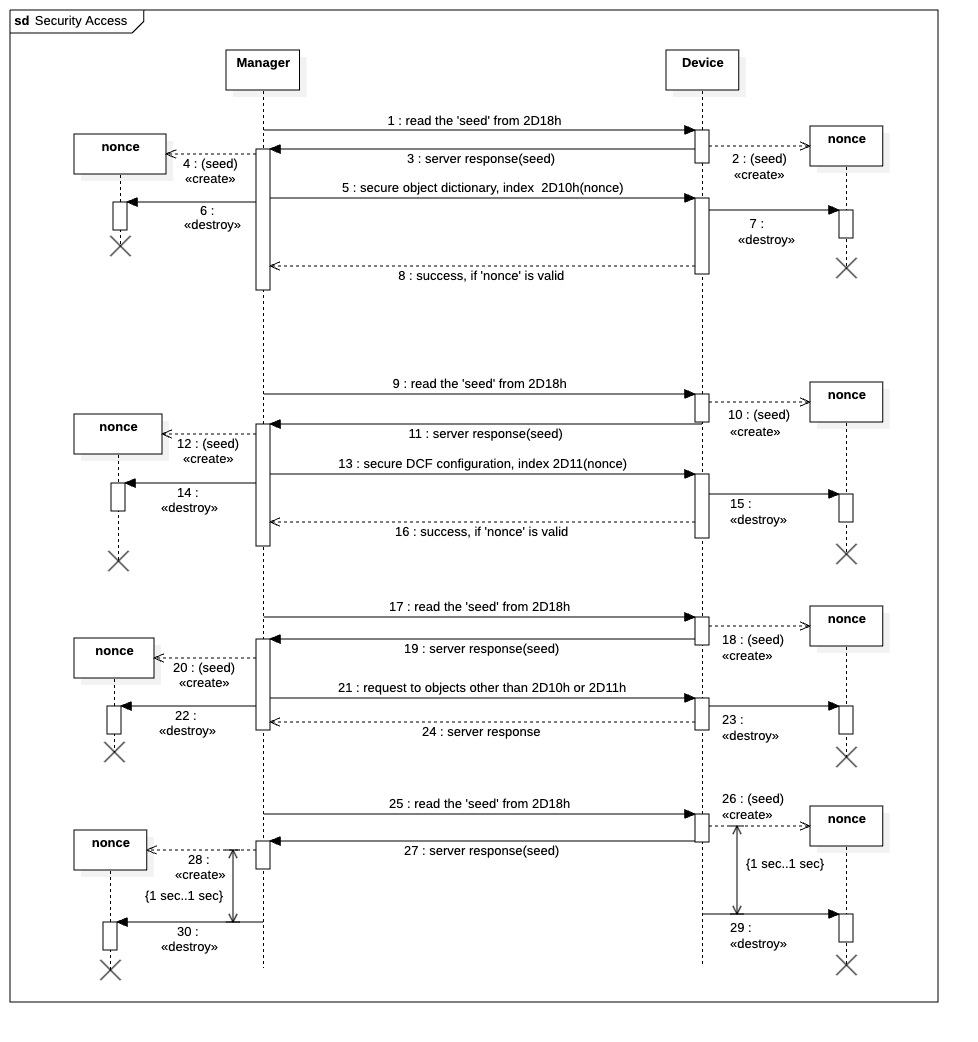
Authentication is achieved using a seed/nonce mechanism, preventing replay attacks and ensuring that only authorised managers can write configuration data (see Figure 4). Once the object dictionary is secured, write access is blocked, and any reconfiguration must be executed through a validated Secure DCF file.
Figure 4: Communication examples for authentication procedure
The server generates a random seed which is used to create a nonce by the server and the manager. The nonce is valid for a maximum duration of 1 second. The nonce can be used only once to gain write access to objects 2D10h and 2D11h. Access to other objects by the CANopen manager will destroy the nonce. This mechanism guarantees the integrity of critical device parameters in sensitive environments.
Conclusion
The secure configuration of CANopen devices offers a robust solution to the growing security demands in medical technology. By combining authentication, integrity checks, and controlled access, medical equipment manufacturers can achieve higher resilience against threats while maintaining compliance with safety standards.
An initial implementation of the Secure Configuration specification has been realised using data elements within the manufacturer-specific area of the CANopen Object Dictionary. This implementation is already operational in a maritime application requiring enhanced security with regard to configuration parameters.
Implementing these mechanisms will be key to ensuring reliable and secure medical systems in the future.
For more information about MicroControl’s solutions for medical equipment, please visit our website or use our contact form to contact us directly.